There’s an easy way to reduce power usage on Linux laptops using Intel’s Powertop utility.
Powertop polls your existing power usage and recommends tunings for your hardware. I’ll show you how to quickly make the most of your battery life using this tool as well as tuned and cpufreq.
Install Powertop
I’m using Fedora for these examples, but most distributions will have this available – adjust as needed.
dnf install powertop -y
Note Normal Pre-tune Power Usage
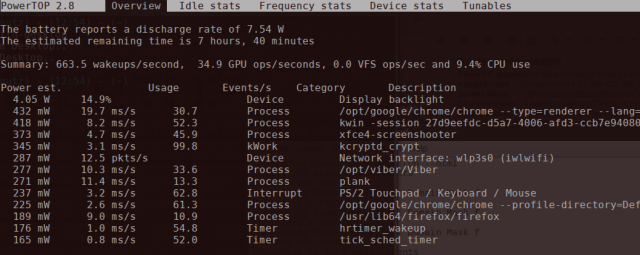
Run powertop to see normal power usage, make sure you are not connected to a power source.
powertop
Poll Usage and Record
Next you’ll want to run powertop with the –calibrate and –html flag while not connected to a power source. Note that –calibrate will disconnect you from wifi temporarily and you might see some screen flickering.
powertop --calibrate
powertop --html
You’ll see some output like below, when it’s completed you’ll have a powertop.html file wherever you ran the program.
Loaded 750 prior measurements
RAPL device for cpu 0
RAPL Using PowerCap Sysfs : Domain Mask f
RAPL device for cpu 0
RAPL Using PowerCap Sysfs : Domain Mask f
RAPL device for cpu 0
RAPL Using PowerCap Sysfs : Domain Mask f
Devfreq not enabled
Preparing to take measurements
unknown op '{'
Taking 1 measurement(s) for a duration of 20 second(s) each.
PowerTOP outputing using base filename powertop.html
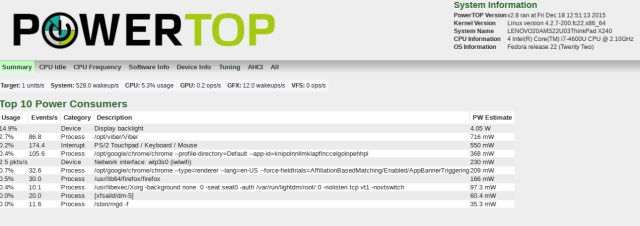
Output and Recommendations
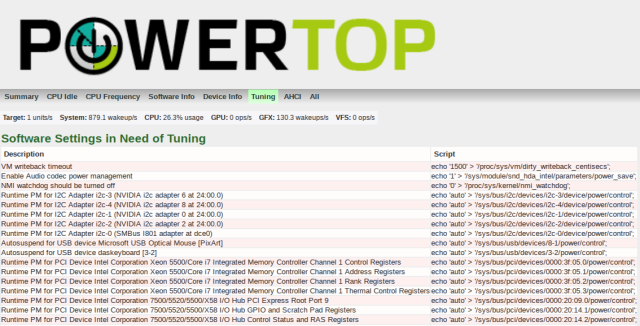
Point a browser to the powertop.html file and you’ll see things like status, power usage, processes using the most power and lastly tuning. The tuning tab is what we’ll focus on.
Apply Tuning Recommendations
There’s several options you can pursue here. You can either manually copy/paste the tuning recommendations from the generated HTML tunings above or you can use lynx and a bit of sed to spit them out and apply them all. Lastly, you can just set powertop to use the –auto-tune feature (though you’ll need to run it at boot everytime). It’s best to review them all prior.
Note: you might want to forgo any USB suspend options if you use an external keyboard or mouse as USB is always slow to resume and this causes issues for some people.
Option #1 – Apply Tuning Recommendations Permanently
In this example I’ll show all tunings in an easy, copy/paste fashion to make the most of your time.
Convert HTML to TXT
lynx -dump -width 200 powertop.html > powertop.txt
Strip out Recommended Power Tunings
cat powertop.txt | sed 's/^.*echo/echo/' | \ sed 's/^.*ethtool/ethtool/' | egrep -B3 "echo|ethtool|hdparm" \ | egrep -v "Software|Description|Script" > /tmp/tuning.txt
Now review what’s been captured, you can paste these them all to apply them or choose individually as you prefer.
cat /tmp/tuning.txt | less
Note the tuning recommendations..
echo '1500' > '/proc/sys/vm/dirty_writeback_centisecs'; echo '1' > '/sys/module/snd_hda_intel/parameters/power_save'; echo '0' > '/proc/sys/kernel/nmi_watchdog'; echo 'auto' > '/sys/bus/i2c/devices/i2c-3/device/power/control'; echo 'auto' > '/sys/bus/i2c/devices/i2c-4/device/power/control'; echo 'auto' > '/sys/bus/i2c/devices/i2c-1/device/power/control'; echo 'auto' > '/sys/bus/i2c/devices/i2c-2/device/power/control'; echo 'auto' > '/sys/bus/i2c/devices/i2c-0/device/power/control'; echo 'auto' > '/sys/bus/usb/devices/8-1/power/control'; echo 'auto' > '/sys/bus/usb/devices/3-2/power/control'; -- snip --
Review the tunings.
If you like how this looks, you can also make a script to apply it all instead of pasting it.
echo '#!/bin/bash' > /tmp/tuning.sh cat powertop.txt | sed 's/^.*echo/echo/' | sed \ 's/^.*ethtool/ethtool/' | egrep -B3 "echo|ethtool|hdparm" \ | egrep -v "Software|Description|Script" >> /tmp/tuning.sh
Run the Script
chmod +x /tmp/tuning.sh sh /tmp/tuning.sh
Option #2 – Auto Tune
Powertop provides the option to simply apply all the recommended settings for you, but they will be lost on boot.
powertop --auto-tune
Persist after boot
You can use the following systemd unit file to simply make powertop a systemd-controlled service
cat > /etc/systemd/system/powertop.service << EOF [Unit] Description=Powertop tunings [Service] Type=idle ExecStart=/usr/bin/powertop --auto-tune [Install] WantedBy=multi-user.target EOF
systemctl enable powertop
Running Powertop
You can run powertop manually at any time to get a feeling for your battery usage. It might be a good idea to see before/after improvement. For comparison I get an average of 6 to 8W of power usage under a normal workload on my Lenovo x240 running Fedora 22 on Kernel 4.2.7. I believe I average around 6-9W, down from 10-12W with no tuning – quite an improvement!
Tuned: Further Savings
You can also use a tuned profile to provide additional power management savings.
Install tuned and Profiles
dnf install tuned-profiles-compat tuned -y
Enable Tuned and Set Profile
systemctl enable tuned.service systemctl start tuned.service tuned-adm profile laptop-battery-powersave
You can list other profiles available and see what works best, just “powersave” is good too.
tuned-adm list
Alternative to tuned profiles – there is also a command called powertop2tuned that will generate a tuned profile based directly on your powertop –html output, you can specify an existing html file or run it without options and it will create one. I just use the laptop-battery-powersave tuned profile instead. Below is an example where powertop-settings is the new tuned profile you’d want to use.
powertop2tuned powertop-settings
Running PowerTOP, please wait... Generating shell script /etc/tuned/powertop-settings/script.sh Generating Tuned config file /etc/tuned/powertop-settings/tuned.conf
Now apply the tuned profile based on powertop settings, you’d use what you named it above.
More info can be found here.
tuned-adm profile powertop-settings
Cpufreq – Further Tuning
Lastly, you will want to enable cpufreq so you can have CPU frequency scale up and down based on demand – this will save a noticable amount of power basd on the powersave profile.
Install cpufreq-utils
dnf install cpufreq-utils -y
Use Powersave Options
cpupower frequency-set -g powersave
Check your settings
cpupower frequency-info
analyzing CPU 0:
driver: intel_pstate
CPUs which run at the same hardware frequency: 0
CPUs which need to have their frequency set by software: 0
maximum transition latency: 0.97 ms.
hardware limits: 800 MHz - 3.30 GHz
available cpufreq governors: performance, powersave
current policy: frequency should be within 800 MHz and 3.30 GHz.
The governor "powersave" may decide speed to use
within this range.
current CPU frequency is 800 MHz (asserted by call to hardware).
boost state support:
Supported: yes
Active: yes
Kernel GPU Savings Options (NOTE i915 chipset only)
I also use the following kernel options for my laptop, a Lenovo x240 using the Intel i915 chipset. These settings won’t work for everyone so research them before applying. If you’re not sure skip over this part.
- file: /etc/default/grub
- Note: this is a snippet, so make sure to append this only to your existing grub settings.
--snip append to your grub entry -- GRUB_CMDLINE_LINUX="drm.debug=0 drm.vblankoffdelay=1 i915.semaphores=1 i915.modeset=1 i915.use_mmio_flip=1 i915.powersave=1 i915.enable_ips=1 i915.disable_power_well=1 i915.enable_hangcheck=1 i915.enable_cmd_parser=1 i915.fastboot=0 i915.enable_ppgtt=1 i915.reset=0 i915.lvds_use_ssc=0 i915.enable_psr=0 vblank_mode=0 i915.i915_enable_rc6=1" --snip append to your grub entry --
Like usual, to apply grub changes run the following command and reboot:
grub2-mkconfig -o /boot/grub2/grub.cfg
Additional i915 Only Tunings (Lenovo x240 or similiar)
You can also pre-blacklist some modules not really needed often and force some power savings i915 kernel module options like below. These seem to further help power savings for the GPU. Note some of these are duplicated in the above kernel boot options, but we’ll force them anyways for modprobe as well for good measure.
cat > /etc/modprobe.d/x240-i915.conf << EOF options i915 i915_enable_rc6=1 i915_enable_fbc=1 lvds_downclock=1 options iwl_wifi power_save=1 power_level=3 bt_coex_active=0 11ndisable=1 blacklist sierra_net blacklist cdc_mbim blacklist cdc_ncm blacklist btusb EOF
Further Power Savings Tips
In general the following tips apply to conserving battery:
- Don’t use max brightness, this seems to usurp a lot of battery power.
- Unplug your laptop when it’s fully charged, in general this prolongs the battery lifetime.
- Use a blank screensaver.
- Disable your ethernet kernel module if you don’t use it often, I do this via rc.local:
touch /etc/rc.d/rc.local echo '#!/bin/bash' >> /etc/rc.d/rc.local chmod +x /etc/rc.d/rc.local echo 'rmmod e1000e' >> /etc/rc.local systemctl enable rc-local.service
- Think about using my hybrid suspend on Linux guide.
TLP
Some readers over at the r/linux subreddit have pointed out that TLP is a good alternative tool to, or to be used in conjunction with powertop. I’ve not tried it yet, being happy with my power savings from the above approach but please post in comments if you have any suggestions and I’m happy to merge them here. Both TLP and powertop will make the same settings, but I prefer to use the powertop approach as it’s usually best to understand/review everything you’re changing before making any changes to the system.